

Virtual Private Networking allows you to securely utilize the public Internet for transmitting your sensitive corporate information.
 |
||
 |
 |
 |
 |
||
virtual private networking
VPN Access
Servers
and Virtual Private Networking
Changing the Face of
Wide-Area-Networks and Remote Access
In less than a decade remote network access has grown from a futuristic notion to a vital element of almost every corporate network. Thanks to the global reach of the Internet, corporations can now hire professionals from a talent pool that covers the entire country or even the world. Field sales people can use corporate network resources to boost efforts in their own territories. By sharing network communications, suppliers can strengthen their bond with customers, and consultants can remove more barriers between their services and their clients. Analysts estimate that as many as eight million people telecommute in one way or another. E-mail and World Wide Web services have become linchpins of corporate communications, and laptop computers are a simple fact of life for anyone who moves on the job.
As these factors fuel the demand for remote access capability, companies are seeking ways to provide greater connectivity at lower cost and with fewer administration and maintenance hassles. All this, of course, without sacrificing the requirements of on-demand service from anywhere in the world. That's where Virtual Private Networking (VPN) technology, such as that used in the VPN Access Servers from Cisco Systems and other vendors come into play.
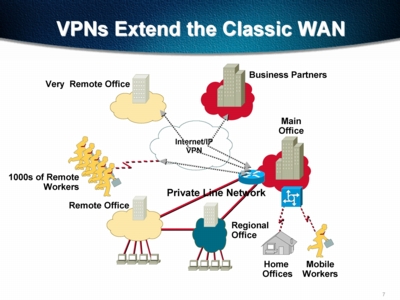
The Remote Access Dilemma
The traditional remote access model was simple enough. Have users dial into a bank of modems to establish a connection, and then have the modems route the connection through a port on a remote access server and onto the corporate network. While such systems allowed the pioneers of remote access to gain the functionality they needed, they also came with a hefty price tag. Not only did customers have to bite the bullet in order to purchase a remote access server; they also had to pay long-distance charges for every remote user. In addition, the corporate MIS department felt the strain. To them, remote access meant a serious time drain. Many network managers report that remote access configuration and support can take up more than half of their on-the-job time.
VPN: A Better Way
VPN technology allows companies to reduce remote access costs by removing
the remote connection from the phone company and "outsourcing" it to the
Internet. The remote user, then, connects to corporate network resources
through a local Internet Service Provider (ISP) rather than over expensive
phone lines. This application eliminates long-distance phone charges and
allows corporate network managers to hand off administration of remote
access connections to the Internet Service Provider.
In order to offer VPN technology, vendors must address the capabilities of the Internet itself. The Internet is designed for TCP/IP traffic only. However, IPX (Novell) traffic constitutes more than 60% of all local network traffic in the U.S., and though IP use in intranets and extranets is growing rapidly, multiprotocol support is mandatory on most remote access links. Multiprotocol traffic is accommodated through a process called tunneling.
VPN: Remote Access You Can Afford
A VPN tunnel is an on-demand virtual point-to-point connection made through
a public network, in this case the Internet. Once connected, a remote
user can utilize the tunnel to exchange information and access servers
and services on the corporate network. By using the Internet for connection,
you eliminate long-distance charges. A local dial-up to the ISP replaces
the WAN circuit.
| VPN | Traditional RAS | |
| Line Costs for 50 users* | $35,970 | $126,000 |
| Administration of RAS connections** | $24,000 | $108,000 |
| Hardware costs*** | $11,400 | $13,500 |
| Total Cost (capital equipment plus one year's line costs) | $71,370 | $247,500 |
|
* One year's line costs includes monthly phone line + usage charges and Internet account for each remote connection ** Administration charges based on figures from "The Real Costs of Remote Access" by Infonetics Research, Inc. *** Assuming 16 ports / tunnel connections for 50 users (1:3 port / user ratio) |
||
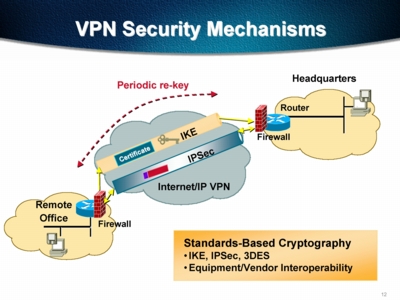
How Tunneling Works
Netalliance recommends the IPSec protocol for maximum application and inter-vendor compatibility. Tunnel servers work by performing three basic operations.
Encapsulation
In order to transmit IP and IPX securely over the Internet, VPN servers encrypt standard IP packets, then
encapsulate the encrypted packets inside another standard IP packet. This IP packet
can then be routed through the Internet to its destination, where the
encapsulation and encryption are stripped off, leaving the original protocol. This process is
completely transparent to your network and applications.
Authentication - For Secure Connection
Authentication is the most important security element of a multiprotocol
IP tunnel. Authentication ensures that tunnels will only be established
between verified tunnel partners. Different tunneling protocols approach
the issue of authentication in different ways. Tunnel authentication
is based on digital signature technology, using the MD5 standard. Digital
signatures allow for continuous authentication on a packet-by-packet basis.
Other popular tunneling protocols rely on PPP authentication routines (CHAP and PAP) to verify tunnel requests. Authentication occurs before the connection is established. Once the connection has been established, however, there is no further authentication of packets. Make sure you know what kind of authentication is provided with any VPN product you consider.
Encryption - For Data Privacy
Encryption is a method of "scrambling" data before transmitting it
onto the wide area link, in this case the Internet. At the remote end,
the data is de-coded using a private "key." Most VPN products support
a range of encryption methods to provide users with security/performance
options. As encryption technology evolves and VPN usage grows, look for
more advanced encryption services to appear
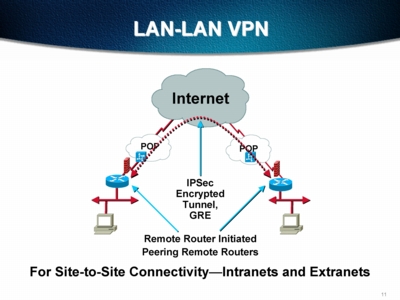
A Comparison of Tunneling Protocols
The Cisco 3XXX and 5XXX concentrators establish secure tunnels using the IETF IPSec standard. IPSec operates at Layer 3 of the OSI model. This means that the VPN concentrator produces straight IP packets that are compatible with every ISP and every IP router in the world.
For additional applications and compatibility, the Cisco concentrators also offer L2TP and PPTP tunneling protocols. The following table provides a comparison between IPSec and L2TP/PPTP.
IPSec [Cisco IOS, 3XXX and 5XXX]
Operational Summary
IPSec allows dynamic, authenticated tunneling via IP-in-IP. Operates at Layer 3 of the OSI model.Authentication
VPN Concentrator uses MD5-based digital signature authentication to prevent session spoofing.Infrastructure Requirements
Client Software at remote user sites. VPN Access Concentrator at central networks. No modification required to ISP equipment.Application Note
Tunnels established by VPN Concentrator do not monopolize Internet connection.
L2TP - Layer 2 Tunneling Protocol [Cisco IOS, 3XXX, 5XXX]
Operational Summary:
L2TP establishes a virtual PPP (Point-to-Point Protocol) connection through the Internet. Operates at Layer 2 of the OSI model.Authentication
CHAP/PAP authentication prior to establishment of tunnel.Infrastructure Requirements
Tunnel peers and all ISP routing equipment must be upgraded to support L2TP in order to recognize and complete L2TP tunneling requests.Application Note
Internet connectivity on both ends of tunnels (when enabled) is limited to the tunnel itself.
RFC’s
Netalliance VPN Access products comply with these IETF standards:
| For IPX Tunneling: |
|
| For IP-in-IP Tunneling or Bridge Tunneling: |
|
| For Security: |
|
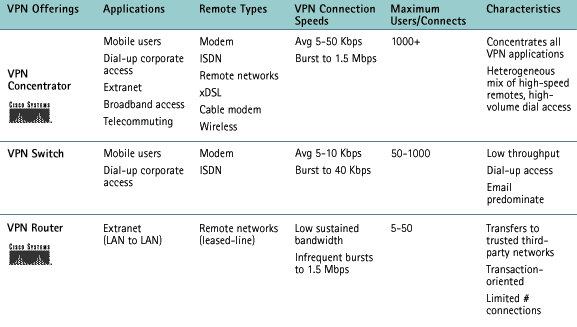
At Netalliance, we offer industrial-strength VPN solutions from Cisco Systems; leaders in wide-area networking technology and VPN solutions. The following
matrix will help you to understand the various offerings in the market today and target the platforms you should
consider:
Cisco Systems 5000-Series VPN Access Servers
The 5000-Series VPN Access Servers, along with the included client software for Windows-XX and Macintosh machines, provides secure access to corporate IP and IPX networks. The VPN Access Server supports up to 1000 simultaneous tunnel connections supporting IP-in-IP and IPX-in-IP encapsulation. Your remote users install Cisco 5000 VPN Client Software on their PCs and make a simple local call to an ISP, eliminating expensive long-distance charges. All tunnel connections utilize the IETF's IPSec and GRE standards for encapsulation as well as MD5 digital signature authentication, and DES and 3DES (Data Encryption Standard) encryption. These features make the 5000-Series VPN Access Servers one of the most cost-effective secure remote access solution available today.
Cisco Systems 3000-Series VPN Concentrators provide a scalable virtual private network (VPN) solution for customer premise and service provider environments. The VPN Concentrator Series supports remote access, LAN-to-LAN and Extranet applications and is specifically focused at addressing bandwidth-intensive broadband connections. It supports a wide range of client software including the Cisco 3000 VPN Client (IPSec), Windows Dial-up Networking (PPTP), and Windows 2000 (L2TP over IPSec). Combining high availability and high performance, the VPN Concentrator Series supports up to 5000 concurrent sessions. These connections are exemplary of emerging high performance desktop applications, such as real-time graphics and integrated voice, video and data, as well as the new breed of high-speed remote connections, such as cable and digital subscriber line (DSL). Specifically designed for corporations that require secure access for their remote employees, partners and customers via the Internet, the 3000-Series VPN Concentrators are based on an open standards approach that complements customers' existing network architecture The 3000-Series VPN solution is manageable through an embedded HTML server with SSL support that can be accessed using a standard web browser of your choice. For added convenience Microsoft's Internet Explorer and Netscape Navigator are included with Cisco's client software package. VPN Concentrator:
- The Cisco 3060 A high-end VPN product designed for large organizations demanding the highest level of performance and reliability with high-bandwidth requirements from fractional T3 through full T3 or greater and up to 5000 simultaneous sessions. Encryption processing is offloaded to specialized SEP modules.
- The Cisco 3030 A mid-range VPN product designed for medium- to large-sized organizations with bandwidth requirements from full T1/E1 through fractional T3 and up to 1500 simultaneous sessions. Encryption processing is offloaded to specialized SEP modules.
- The Cisco 3005 An entry-level VPN product designed for small organizations or branch offices with bandwidth requirements up to full-duplex T1/E1 and up to 100 simultaneous sessions. Scalable and field upgradeable to either the C30 or the C60. Processing for all tasks shares the system processor.
Cisco Systems IOS can also participate in VPNs. Implemented as a 'feature pack' software upgrade to their IOS operating system,
the amazingly versatile software at the heart of each Cisco router. Depending on the hardware platform, this feature
pack is available with either DES or 3DES encryption technology, and supports the IPSec standards for tunneling TCP/IP
only. A key issue
to consider is that since the encryption engine is software-based, the maximum encrypted throughput is limited by the
CPU horsepower available in the router. Many low- and medium-range routers offered by Cisco do not have sufficient
processor power to handle more than a few simultaneous remote-access client connections or LAN-LAN connections. Contact
Netalliance for more detailed recommendations.
Phone 651-556-9600; Fax 651-645-7550; info@backpack.net
All rights reserved. All material copyright. Netalliance, Inc. © 1995-2005. Updated: June 12, 2008.






































